Phishing: The Sport of the Digital Age; Student Body Falls Victim to Phishing Scam
Colgate students experience problems receiving emails that are trying to retrieve their personal information.
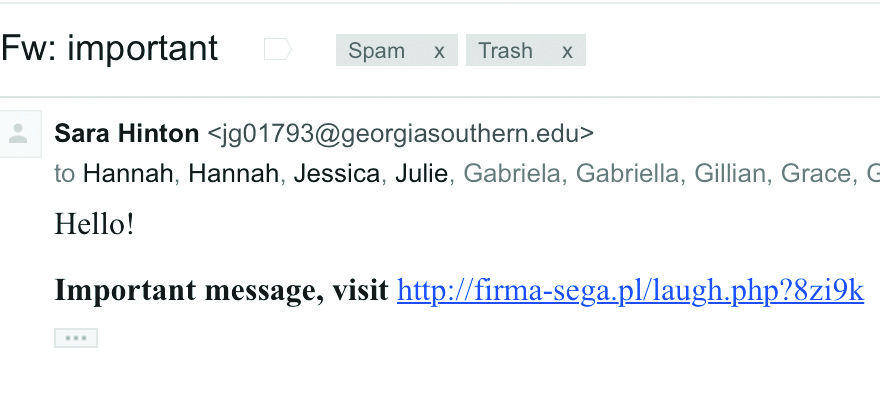
Suspicious emails have been circulating among Colgate’s Gmail network in recent weeks. Many students received messages from their friends’ Colgate email addresses with the subject “Fw: important,” asking them to visit a link in the email. This is the most recent of many phishing scams targeting Colgate students in past years.
Phishing is a form of digital hacking aimed at collecting sensitive information like usernames and passwords, usually with the goal of stealing money or valuable information. Martin Page, a senior who works for Colgate’s Information Technology Services (ITS) noted that usernames and passwords to online games such as World of Warcraft or League of Legends are especially coveted, since players will pay real money for in-game currency or special edition avatars.
Phishers often target large organizations and colleges for several reasons. First, these types of email networks usually assign addresses based on a universal format, like [email protected]. Second, users in these organizations are likely to use email distribution lists, which provide the phisher with more potential victims. Once hackers have access to an email account, they can send their “bait” to users the victim has been emailing or to distribution lists of classes or clubs stored in the victim’s emails.
This is how the latest phishing scam at Colgate has been spreading. Senior Ranissa Adityavarman first noticed a strange email with the subject line “Fw: important” and the body reading “Hello! Important message, visit [link].” The next day she received five more, and then her inbox began to fill with over 50 identical emails from different Colgate addresses.
“I got them from a lot of my friends, then one from Career Services, then one from myself, which was really weird because I know I didn’t send it,” Adityavarman said.
In fact, Adityavarman had not sent the email. Phishers can disguise emails so they appear under a certain name, like Jane Doe, but do not originate from [email protected]. A number of Adityavarman’s friends and members of her sorority had the same experience with their email accounts. Senior Sara Hinton was also surprised to receive the “Fwd: important” email from herself.
Disguising the sender’s name is one of many phishing techniques. Just as fishermen use bait to catch a fish, phishers use carefully crafted emails to trick victims into either divulging their username and password or clicking on a link that will install a virus called Keylogger Trojan, which records everything the victim types on their computer. The odds of acquiring such a virus are low for students with antivirus software, but Page points out that those students are still susceptible to hackers infiltrating their email accounts.
Users can do several things to protect themselves against phishing scams. The first is to carefully inspect emails to assess their validity. Experienced phishers spend time and energy formatting their emails to look credible, using familiar logos and fonts. They also put effort into making the emails’ content believable.
For example, Colgate students in the past have received emails notifying them they are running out of storage space – a seemingly plausible issue for college students with hundreds of emails in their inboxes – and asking for their username and password in order to fix the issue. Sometimes emails like these can be marked “Urgent” and warn users that they must take action within 24 hours or their accounts will be lost. Making these emails appear to be time sensitive is another tactic phishers use to coax victims into reacting quickly, before they have time to verify the email’s legitimacy.
If you receive a suspicious email, Colgate ITS asks that you contact them before entering any sensitive information or clicking on a link. Colgate ITS maintains that they will never send an email asking students for their login information, and to view such emails with caution.
Students who believe their account has been compromised by a phishing scam should contact ITS immediately. However, students may not know their account has been compromised, since hackers often continue to use the original user’s password, rather than change it, in order to avoid suspicion. In addition, there are ways through which the phishers can disguise sent emails so the original user may not be able to view “bait” emails in their Sent box. Marking suspicious emails as “Spam” instead of moving them to the trash folder will help ITS identify future phishing scams.
Lastly, students should take care to change their passwords every six months and ensure that their security questions cannot be easily guessed. If your security question is “What’s your dog’s name?” and you post photos of you and Spot on social media, you run the risk of being phished.